What the Heck is Identity Stitching? Roadmapping the Consumer Journey
Understanding and stitching together digital identities is a crucial aspect of effective customer data management. Identity stitching, or identity resolution, involves connecting disparate data points to create a unified view of individual consumers. This enables businesses to enhance their understanding of consumer behavior, personalize experiences, and drive targeted marketing strategies - but it can be a complex process. It’s particularly challenging in multichannel environments where interactions occur across a wide range of devices, apps, and channels or in large organizations where consumers interact with multiple brands.
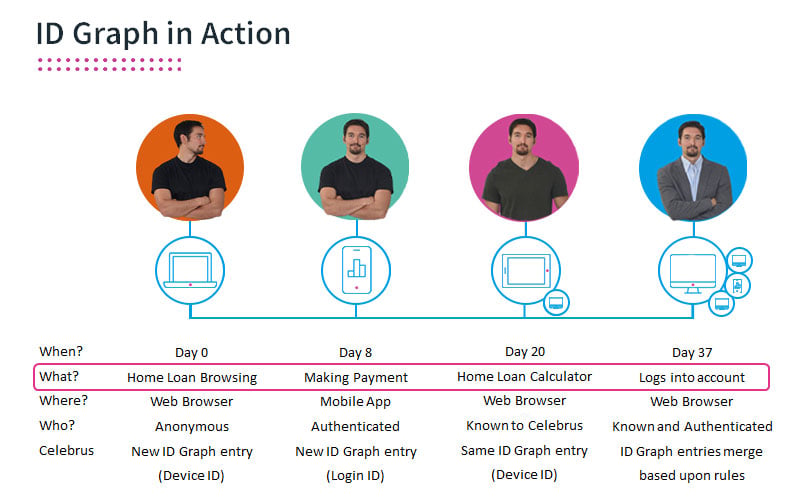
The modern approach to identity stitching involves leveraging a first-party identity graph. This comprehensive graph persists visitor profiles for both known and anonymous browsers, merging anonymous and authenticated profiles by connecting and matching identifiers over time. By layering various identifiers onto a robust data model, businesses create a holistic and accurate representation of their customers' identities.
To be effective, identity stitching must enable real-time identification of ALL visitors, regardless of their authentication status. This means being able to distinguish between anonymous and known customers, connecting their interactions across various sources in real-time, and persisting that identity over time. By doing so, businesses can deliver personalized experiences, validate transactions, and make data-driven decisions that drive positive outcomes.
Another critical factor in identity stitching is the ability to connect identities across multiple channels, devices, and domains. Consumers interact with brands through a variety of touchpoints, such as websites, mobile apps, and social media platforms. And when it comes to large, multi-domain organizations there are additional layers of data to capture. To truly understand the consumer journey, businesses must be able to recognize and stitch these identities together seamlessly.
Consumer journeys aren’t linear – how many times have you visited your bank for example, switching between online and mobile, sometimes logging in and sometimes just doing research? Persisting first-party identity across channels, devices, and domains ensures decisioning systems have the data needed to tailor each experience to consumer preferences and interests in milliseconds – whether the visitor is known during that session or not.
A key differentiator when looking at identity stitching is the ability to persist visitor identity and session data across domains, aka “cross-domain continuance” to ensure you’re building a complete picture of every consumer and every journey. This approach breaks down data silos and establishes a single source of truth for identity and contextualization, creating ideal subsets of audience data that can be connected to downstream systems and enable hyper-specific targeting and customization.
An effective identity stitching solution also accounts for the challenges posed by changing regulations and privacy concerns. As third-party cookies become extinct and browser restrictions increase, businesses must adapt their identity resolution strategies to ensure accurate and privacy-conscious results. First-party data capture is essential, as it enables businesses to own and control their data, ensuring privacy compliance and data security while staying unimpacted by browser restrictions and cookie deprecation. By adhering to a first-party approach, businesses can maintain consumer trust while still gaining valuable insight into their behavior.
Ultimately, identity stitching empowers businesses to create a more personalized and seamless consumer experience. By connecting consumer identities across channels, domains, and devices, businesses gain a deeper understanding of their consumers, identify patterns, and deliver relevant and timely interactions. Whether it's tailoring marketing messages or improving customer support, identity stitching empowers businesses to build stronger relationships with their customers and drive business growth.
How it works
By leveraging a first-party approach, stitching identities across channels, and adapting to changing regulations, businesses gain a comprehensive view of their customers and can deliver hyper-personalized real-time experiences that foster loyalty and drive success. For businesses to succeed, identity stitching isn’t just a luxury – it’s a necessity.
How to implement identity stitching to build a unified customer journey
Identity stitching is a powerful technique that empowers businesses to unify consumer profiles by seamlessly connecting consumer data from all touchpoints. By stitching together different pieces of information, enterprises can create personalized experiences for individuals, tailored to their specific needs and preferences. Done right, identity stitching helps businesses improve visitor engagement and conversion rates.
Implementing identity stitching to build a unified customer journey requires careful planning and execution. Here are some steps to help you get started:
- Capture first-party consumer data in real-time: Start by establishing a first-party data platform that captures ALL data across departments, channels, devices, and domains. Ensure you have a true first-party data capture solution that can build and persist anonymous identity.
- Collect and centralize your data: Gathering all the data you can from various sources, such as CRM systems, social media platforms, mobile apps, and website domains. Centralize this data in a single database or data platform.
- Clean and standardize data: Ensure the data you collect is accurate, up-to-date, and standardized. This will help eliminate duplicates and inconsistencies, making it easier to stitch identities together.
- Identify common identifiers: Look for common identifiers across different data sources, such as email addresses, phone numbers, or social media handles. These identifiers will serve as the basis for stitching identities together.
- Use advanced matching algorithms: Leverage advanced matching algorithms to match and link customer identities across different data sources. These algorithms can handle variations in data formats and identify potential matches even with slight differences.
- Create a unique identifier: Once identities are stitched together, assign a unique identifier to each individual. This identifier will be used to track and analyze consumer behavior across different touchpoints.
- Personalize experiences: With a unified consumer journey, businesses can deliver personalized experiences based on the stitched identities. Use the consumer data to segment your audience and tailor your marketing messages and offers accordingly.
- Continuously update and refine the consumer journey: As new data becomes available, update and refine the stitched identities to ensure accuracy. Regularly analyze consumer behavior and feedback to optimize the journey and drive better results.
By following these steps and adapting them to fit your specific business needs and goals, you can create a seamless and personalized consumer journey that enhances engagement and boosts conversion rates.
By leveraging a first-party data platform, stitching identities across channels, and adapting to changing regulations, businesses gain a comprehensive view of their customers and can deliver hyper-personalized real-time experiences that foster loyalty and drive success. For businesses to succeed, identity stitching isn’t just a luxury – it’s a necessity.

